We believe your privacy is very important. We use cookies to track your behaviour and provide a better experience
Backend Helpers | Automation and Software Development for Cloud Applicationses
Introduction to HashiCorp Vault

Vault is a tool for secrets protection. These secrets include passwords, access keys, etc. This tool also provides access management and log auditing. In this post we are going to learn common how to use Vault to perform basic CRUD operations over encrypted key value pairs of data.
Relevant Features
- Secure Secret Storage: Data is encrypted before being written to disk.
- Dynamic Secrets: Secrets can be created and requested programmatic by external applications.
- Data Encryption: Encryption and decryption happens in memory, no data storing is required.
- Leasing and Renewal: Vault can renew and revoke secrets.
Installation
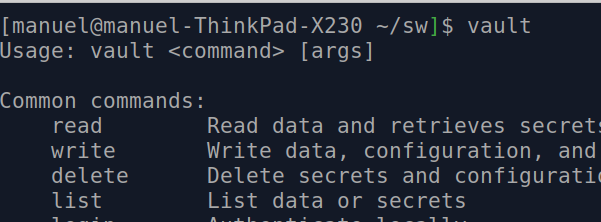
You need to download vault and add the location of this file to the $PATH environment variable. You can verify the installation by running the following command:
vault
Starting The Development Server
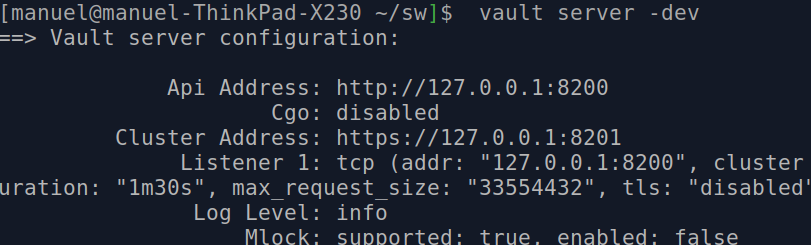
Vault's default installation includes a simple development server. Please be aware that this server is not suitable for production . The following command starts the development server:
vault server -dev
Configuring the client
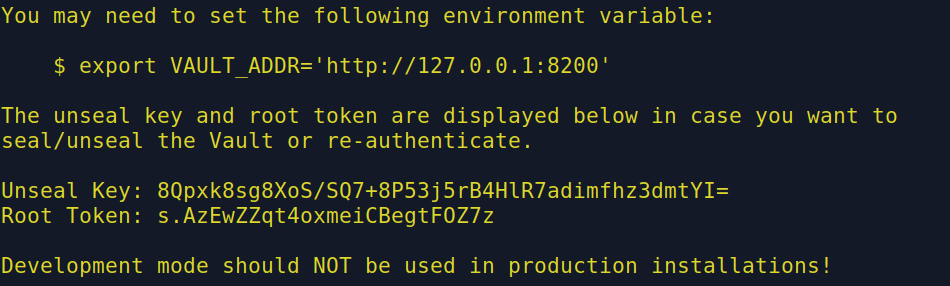
Open another terminal and setup the $VAULT_ADDR environment variable by running the following command:
export VAULT_ADDR='http://127.0.0.1:8200'
You also will need to set up the generated root token as an environment variable:
export VAULT_DEV_ROOT_TOKEN_ID="s.AzEwZZqt4oxmeiCBegtFOZ7z"
Verifying if the Server is Running
The next command checks if the server is running and the client properly configured:
vault status
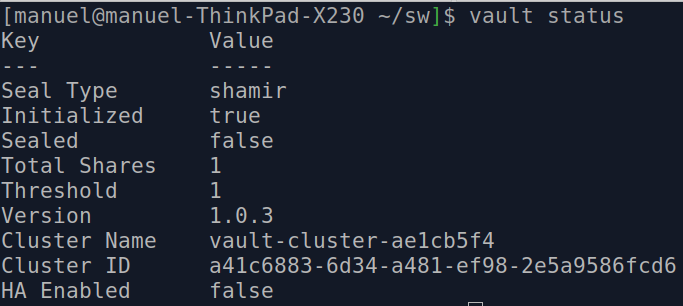
Managing Secrets
The development server provides a full implementation of the Vault HTTP API . We will use the console client in the next sections to create, get and remove secrets.
Step 1: Write a Secret
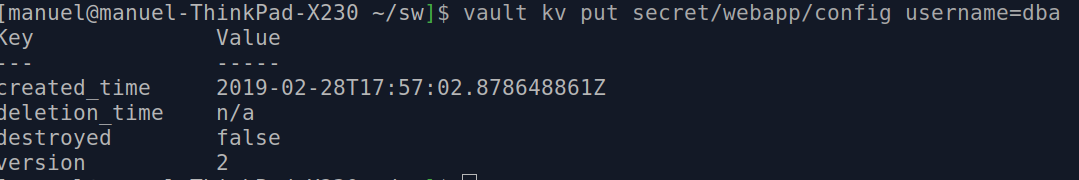
The following command writes a secret, remember that vault is a key,value pair based system:
vault kv put secret/webapp/config username=dba
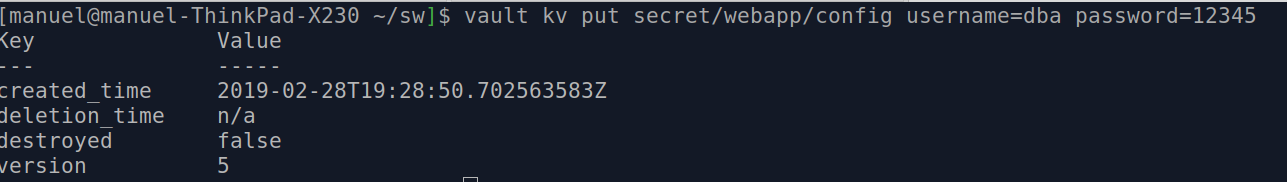
You can also push multiple values for every key:
vault kv put secret/webapp/config username=dba password=12345
Step 2: Query a Secret
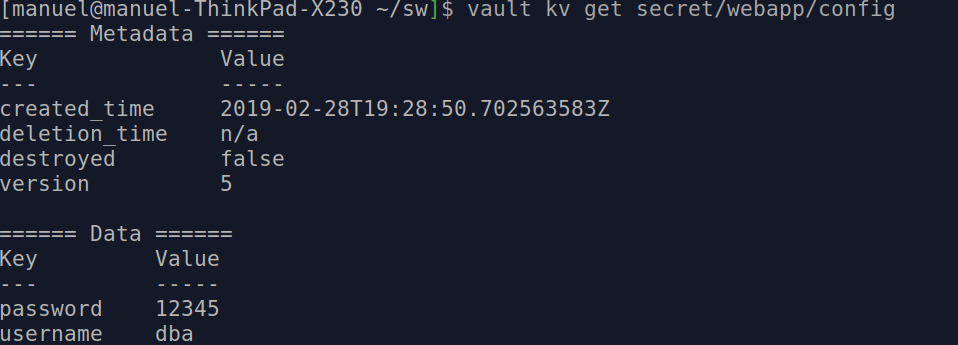
The next command asks vault for a given secret:
vault kv get secret/webapp/config
You can use the next command to get only the value you're asking for:
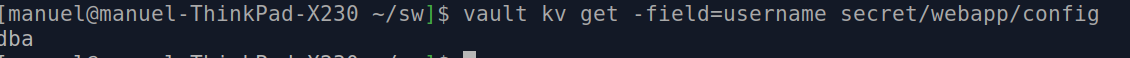
vault kv get -field=username secret/webapp/config
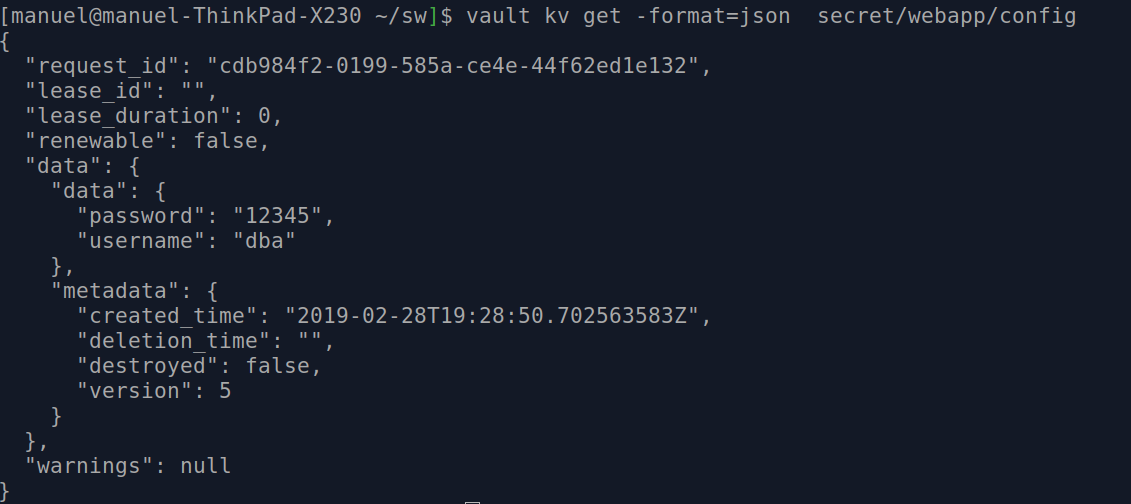
The following command returns the value in json format:
$vault kv get -format=json secret/webapp/config
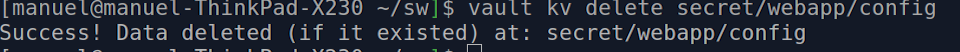
Delete a Secret
The next command may be used to delete a key:
vault kv delete secret/webapp/config